Your Customers Expect The Best, And Voctiv Delivers Rock-Solid Performance
Enterprise-Grade Security Meets Unlimited Scalability
Managing high-growth scenarios requires confidence in your technology foundation. Voctiv's platform processes over 3M minutes of traffic monthly, scaling seamlessly during peak periods while maintaining bank-level security standards. Our architecture supports 15,000 simultaneous connections per installation, with unlimited horizontal scaling capabilities.
Leading global enterprises trust Voctiv with their most sensitive customer interactions. Our platform is built on a secure, fault-tolerant architecture with 99.9% availability, supported by real-time monitoring and automated failover systems. From data encryption at rest and in transit to comprehensive access controls, we maintain the highest security standards while delivering exceptional performance at any scale.
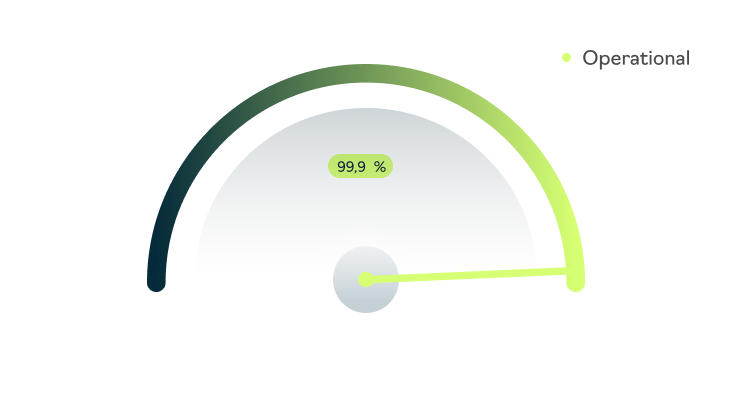
Consistent 99.99% Uptime
In the world of customer communications, every second of downtime can mean lost opportunities and damaged trust. Voctiv's platform is engineered for ultimate reliability, maintaining 99.99% uptime through a robust, fault-tolerant architecture. Our system achieves this through N+1 redundancy across all critical components, automated failover mechanisms, and real-time health monitoring.
The platform's distributed architecture enables seamless performance even during maintenance windows or unexpected challenges. Every customer interaction is protected by multiple layers of redundancy, ensuring business continuity for enterprises that can't afford to miss a single customer connection.

Built Following ISO Security Standards
Voctiv's platform architecture and processes are designed following international security best practices and ISO guidelines for information security management. Our development and operations teams implement comprehensive security controls aligned with ISO 27001 framework principles, including robust data protection, access management, and security monitoring.
The platform incorporates industry-leading security practices across all key areas: secure development lifecycle, encryption of data at rest and in transit, comprehensive access controls, continuous security monitoring, and incident response protocols. While we continue to enhance our security framework, we maintain strict adherence to global security standards and data protection requirements that our enterprise customers expect.




